
It’s hard to figure out what the actual threats are, and the sheer number of alarms can overwhelm most users. Run Trivy on a pod using an Nginx image and you’ll easily get 50+ warnings!
That is why we decided at K8studio to build our own security tool for Kubernetes.
In our incoming 3.2.0 Release we have done a number of things: 1.If is not reachable it’s not hackable:
When we do a security audit of a cluster, probably the first thing we look at is the network. If we run a penetration test and have an IP address, the most obvious thing to do is run an Nmap scan to see what ports are open. That’s why, when we talk about security, the first thing you want to understand is what entry points a hacker could exploit.
In this new version of K8studio, we’ve added a view in our visualizer that lets you see exactly that right away. You can instantly check what services and ingresses are open to the public.
Just click the DevSec switch, and you’re there.
Now you’ll be able to see the cluster from a whole new angle — a security perspective. One thing you’ll notice is that in our visualization, we clearly mark the entry points and show you which services are publicly available.

Once we know the entry points, we can follow the path to see which workloads are reachable. The visualization also highlights what’s vulnerable.

If we click on a deployment, go to our editor, and click on the Security tab, we can get a deeper understanding and see detailed information about the vulnerabilities that have been found.

Here, we’ve done quite a bit of work:
- Added a summary of the security status of each workload, ranked from 0 to 100.
- Introduced tags that give an idea of what a hacker could accomplish, like escape-host, data-theft, privilege-sa, cluster-escalation, workload-injection, and read-secrets.
- Provided a clear, human-readable explanation for each vulnerability, including a detailed list with descriptions and recommendations.
- On the Security tab, you’ll also find the security account info with bound roles and a permission table.
- Included a security context overview to understand which user the container runs its processes as, and what privileges it has.
- And importantly, added a Network Policy tab where you can see if any network policies are restricting ingress or egress access.
2. Understanding your Kubernetes network.
One of the great things about Kubernetes is that it’s designed so everything can connect to everything. But at the same time, this creates one of the biggest nightmares for anyone trying to secure a cluster.
Kubernetes gives us Network Policies as a tool to firewall access and restrict network traffic. But Network Policies are hard to manage especially in a complex cluster. They rely on labels, and you can have multiple policies affecting the same workload.
When you just see them as a list, it’s really tough to understand what can connect to what, and what the final combined effect of all these policies is across the cluster. In our opinion, this is one of the biggest challenges we face when auditing a client’s cluster.
That’s why we’ve added three new features in K8Studio:
- Network Policy Navigator — In DevSec Ops mode, you can click on any workload and instantly see what it can connect to — and who can connect to it. You’ll know right away whether it’s restricted or wide open. This is where, for me, the power of CloudMap visualizations really shines.
- Workload Network Policy View — In the workload editor, you can now see exactly which network policies are affecting a given workload.
- Network Policy Impact View — In the network policy editor, you can now see which workloads a specific network policy is affecting.
These features make a real difference when it comes to understanding your network and checking whether it’s secure.
3. Comprehensive Security Dashboard.
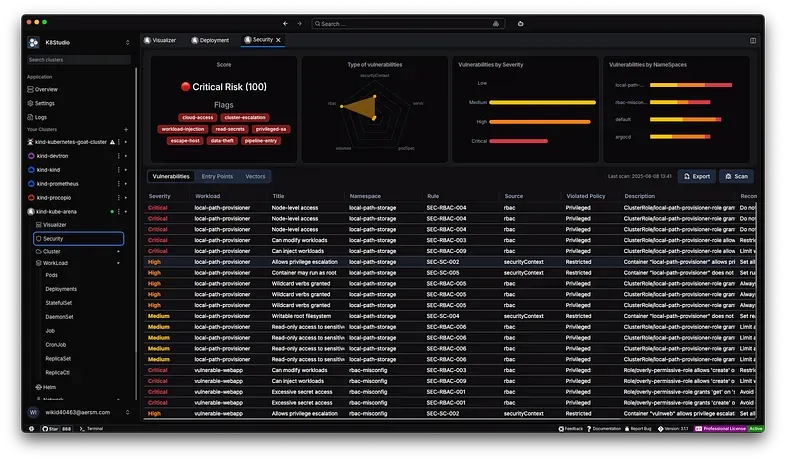
To finish, we’ve also added a Security Dashboard. Here are its main features:
- Vulnerabilities List — where you can search, filter, and sort by severity, namespace, type, and tag.
- Entry Points List — showing all publicly open services.
- Possible Security Vectors — since K8Studio has full data on the cluster, we build a directed graph combining network policies and entry points. Taking into account the vulnerabilities of each node (workload), we can calculate potential attack vectors across the cluster.

We really would like to know what you think about these new features.
Thank you ….
