K8Studio: DevSec View for Kubernetes Security Insights
Many Kubernetes security tools are cumbersome. Take Trivy, for example: it requires installation, consumes cluster resources, and floods your environment with CRDs. Even on a relatively healthy cluster, a single Nginx pod scan can produce 50+ warnings — most of which aren’t actionable. The result? Alert fatigue, distracted engineers, and difficulty separating real threats from noise. That’s why we built **DevSec View** into K8Studio. Instead of drowning you in alarms, it gives you an instant, contextual security perspective: what’s exposed, what’s vulnerable, and what’s exploitable. Just flip the DevSec switch and immediately see your cluster from a hacker’s point of view.
With DevSec View, you can:
If it’s not reachable, it’s not hackable.
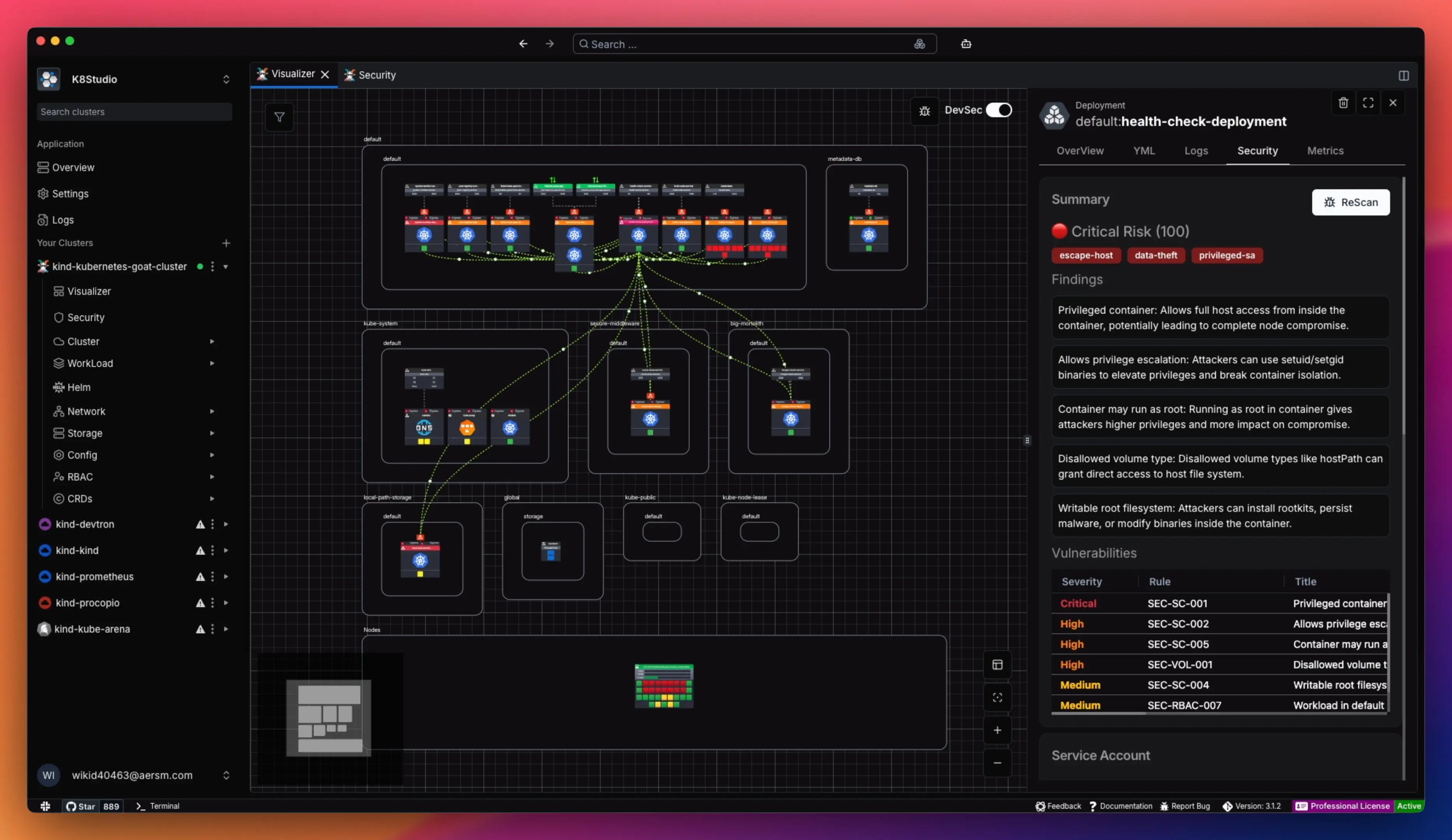
Security starts with exposure. Our visualizer marks public entry points — services and ingresses that are accessible from outside your cluster. From there, you can trace which workloads are reachable, and whether vulnerabilities in those workloads are exploitable. This mirrors a real attacker workflow: scan open ports → identify entry → escalate. Now you see that instantly, without guesswork.Deeper vulnerability insights.
Open a workload in the editor, switch to the Security tab, and get a clear breakdown:- A security score (0–100) for quick risk assessment.
- Hacker-oriented tags like escape-host, data-theft, privilege-sa, cluster-escalation, workload-injection, read-secrets — so you understand what an attacker could actually do.
- Readable explanations & recommendations (not just CVE IDs).
- Security account info showing bound roles and permission tables.
- Security context overview: which user runs the container, what privileges it has, and whether it’s running too broadly.
Network Policy Clarity.
Kubernetes’ default networking model allows everything to talk to everything — a security nightmare.
Network Policies fix that, but they’re notoriously hard to manage. Policies are label-based, overlapping, and when viewed as a flat list it’s almost impossible to understand their combined effect.That’s why we added three dedicated tools:
- Network Policy Navigator — click any workload and instantly see what it can connect to, and who can connect to it.
- Workload Policy View — understand exactly which policies affect a given workload.
- Policy Impact View — see which workloads are governed by a particular policy.
These features make network security visible and manageable, not just YAML guesswork.
Lessons from the trenches.
While developing DevSec View, we discovered just how complex policies can be. Writing unit tests to validate network-policy → workload mappings took over 120 test cases!- Some policies use empty selectors (
podSelector: {}) to apply globally in a namespace. - Others rely on exact label matches or
matchExpressionsfor more complex selection. - CNI plugins like Calico and Cilium even introduce global policies beyond namespace scope.
These nuances make it hard to know what’s really protected — which is why we built the CloudMap visualization to surface whether a workload is actually restricted or wide open.
- Some policies use empty selectors (
Bottom line:
DevSec View transforms Kubernetes security from an endless list of CVEs into a contextual,
visual map of risks. You see entry points, attack paths, vulnerabilities, permissions, and
network restrictions — all in one place.
Instead of wasting cycles on noise, you focus on the issues that matter most for protecting your cluster against real-world attacks.